The Splunk integration with Lumeta requires the installation of two files and the addition of a Lumeta input. Both of these are performed on your Splunk server.
- Download the two zipped application files (attached to this page) to your local system:
- Unzip them.
Now you are ready to perform the installation in Splunk.
Installing the Lumeta Application in Splunk
To install the Lumeta plug-in to Spunk:
...
Configuring the Lumeta Application in Splunk
...
Add the Lumeta URL:
...
https://3.9.250.98/api/rest/report/savedQuery
...
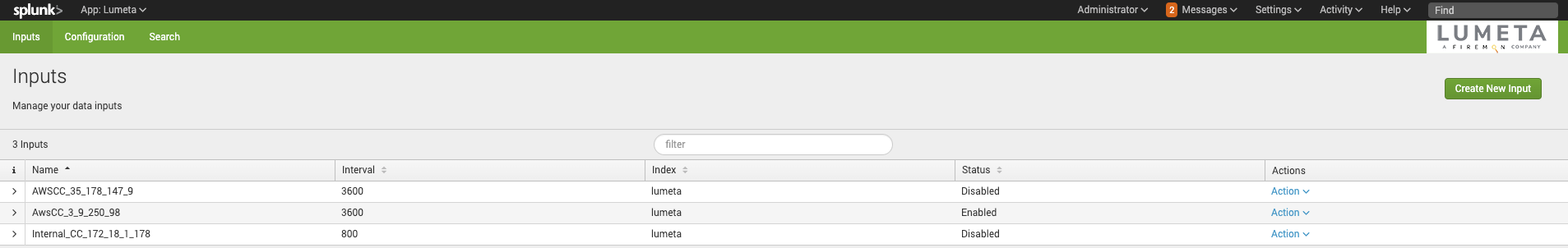
The connection is made and the new input is added to the list:
...
Select Action > Enable to power on the connection.
View Select syslog Data
To search syslog data from Lumeta To view selected syslog data from Asset Manager in Splunk:
- On the Splunk Apps page, select Lumeta App for Splunk.
- Select the Search tab (if you are not there already).
- Enter your search criteria. Examples follow:
- source=”tcp:9997”
- index=lumeta
- sourcetype=”lumeta_log_parser”
- now combine all 3 into one search
- index=lumeta sourcetype=”lumeta_log_parser” source=”tcp:9997”
View Dashboards
To view Lumeta dashboards in Splunk:
...
...
index=lumeta sourcetype="lumetaapiparser" *|table "Account ID" "Instance ID" "Public IP Address" Provider numberofinterfaces Name Region securitygroupsids{}{} | where numberofinterfaces not null and Provider not null and Name not null and Region not null| rename securitygroupsids{}{} as securitygroupsids
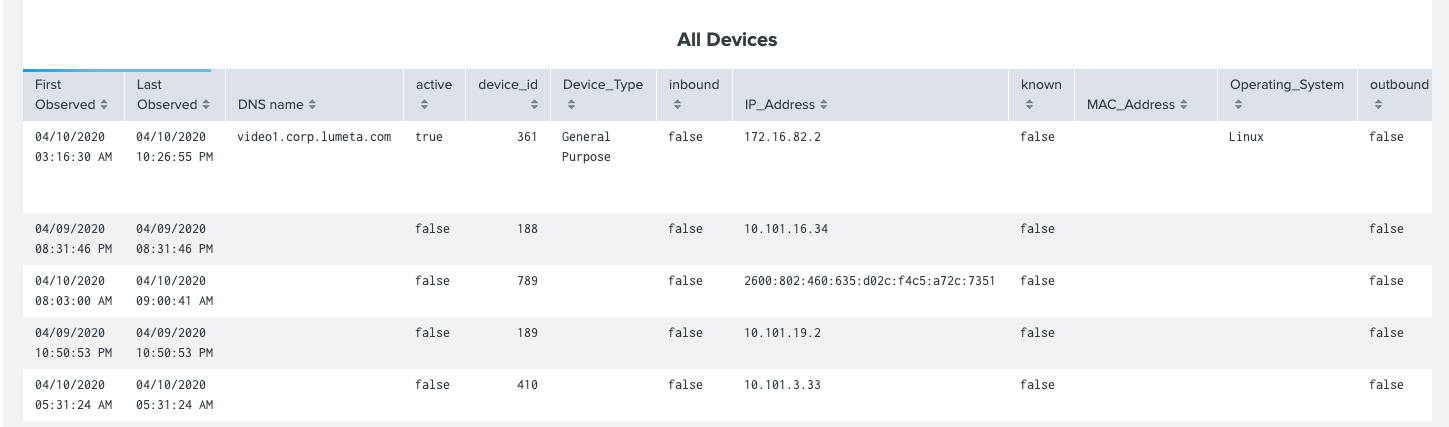
index=lumeta sourcetype=lumetaapiparser * |table "First Observed" "Last Observed" "DNS name" active device_id Device_Type inbound IP_Address known MAC_Address Operating_System outbound scantypes{} protocols{} snmpaccessible snmpresponder target vendor version zoneid zonename| search "First Observed"=* OR "DNS name"=* OR "Last Observed"=* OR active=* OR device_id=* OR Device_Type=* OR inbound=* OR IP_Address=* OR known=* OR MAC_Address=* OR Operating_System=* OR outbound=* OR scantypes{}=* OR protocols{}=* OR snmpaccessible=* OR snmpresponder=* OR target=* OR vendor=* OR version=* OR zoneid=* OR zonename=*
index=lumeta sourcetype="lumetaapiparser" |table os count time| fields - time
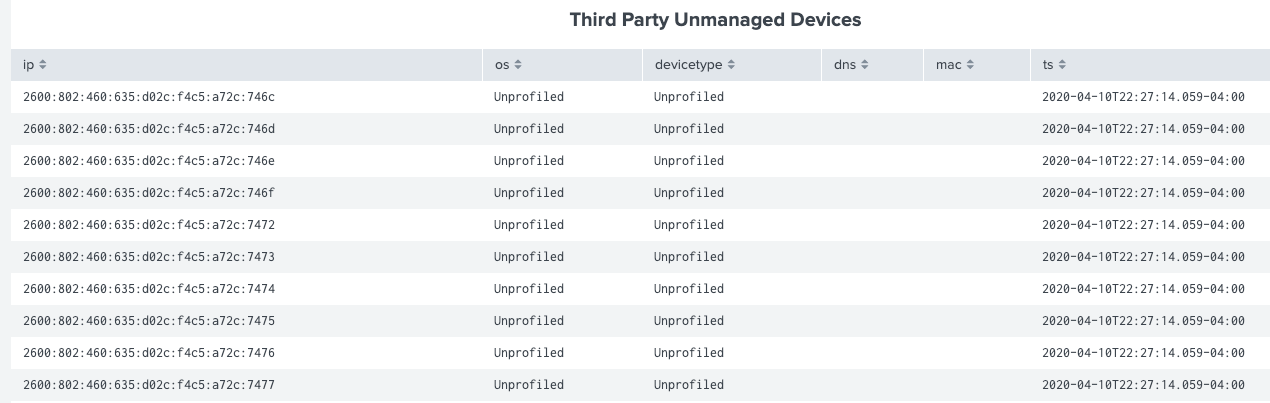
| where count not null and os not nullindex=lumeta sourcetype="lumetaapiparser" * source_name=* | table ip os devicetype dns mac ts
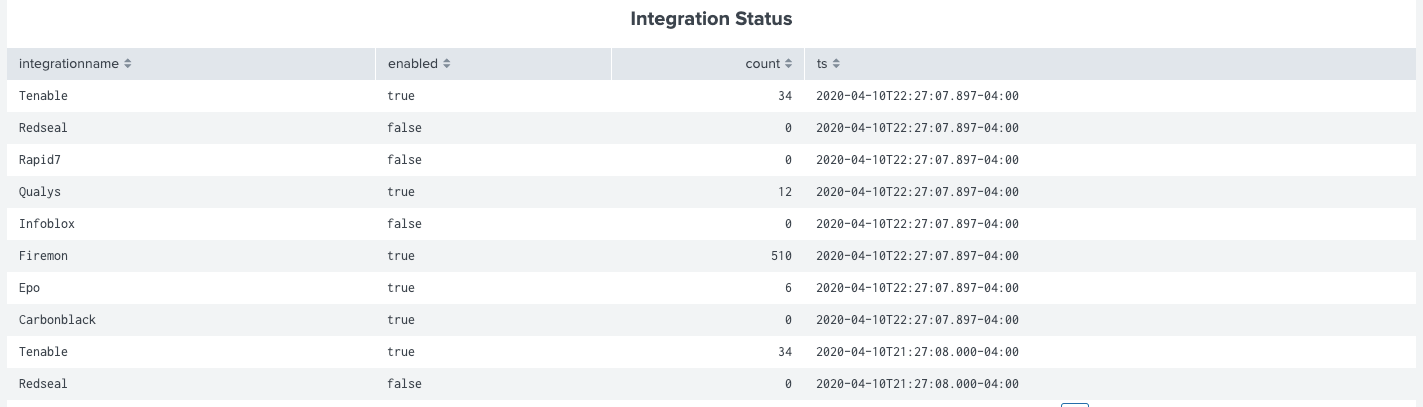
- index=lumeta sourcetype="lumetaapiparser" * |table integrationname enabled count ts|where integrationname not nul