...
| Lumeta Enterprise Edition 4.3 | |
|---|---|
The upgrade file is available now in FireMon User Center > Downloads. | For the upgrade procedure, seeUpgrading to Lumeta Enterprise Edition 4.3. |
| Warning | ||
|---|---|---|
| ||
Before upgrading to 4.3 speak with you SE or contact support at lumetasupport@firemon.com to verify your database encoding. Firemon Support will supply a script the end user can run to check that their database is properly encoded. |
We recommend that you upgrade your Lumeta Enterprise Scouts when you upgrade your Command Center. However, Enterprise Scouts 4.1x and later are compatible with the 4.3 version of the Command Center.
...
| Tip | ||
|---|---|---|
| ||
Lumeta uses version 1.2 of Log4j which is unaffected by CVE-2021-44228 as the JndiLookup Class required for this vulnerability to be exploited was not made available until Log4j version 2.x. For more information, jump to Security Advisories. |
Documentation
On the main menu, we've added a Help tab from which you can access the Lumeta API Reference in Swagger and this Support site, https://lumetadocs.firemon.com/.
Database Update
The Lumeta 4.3 platform uses PostgreSQL 13 database, which is an upgrade from PostgreSQL 9.6.
Scout Enhancements
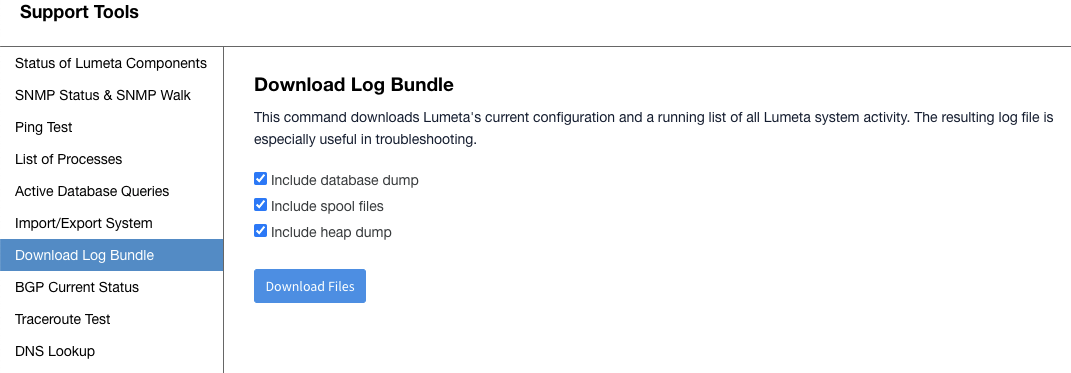
A variety of support tools previously available only on Command Centers, including the capability to download a log bundle, are available from your Enterprise Scout GUI. On your Enterprise Scout, navigate to Settings > Support Tools to see the additions.
Integration with Security Manager
Lumeta's integration with Security Manager has been enhanced as follows:
- All devices for which interface data is present, regardless of whether route data is present, are forwarded to FireMon Security Manager.
- Devices pushed from Lumeta to Security Manager are labeled by their "sysname" rather than their IP address. The IP Address is already listed under the Management IP column.
- Lumeta does not push 0.0.0.0/0, which would allow traffic from any IPv4.
- Lumeta removes duplicate devices before pushing them to Security Manager.
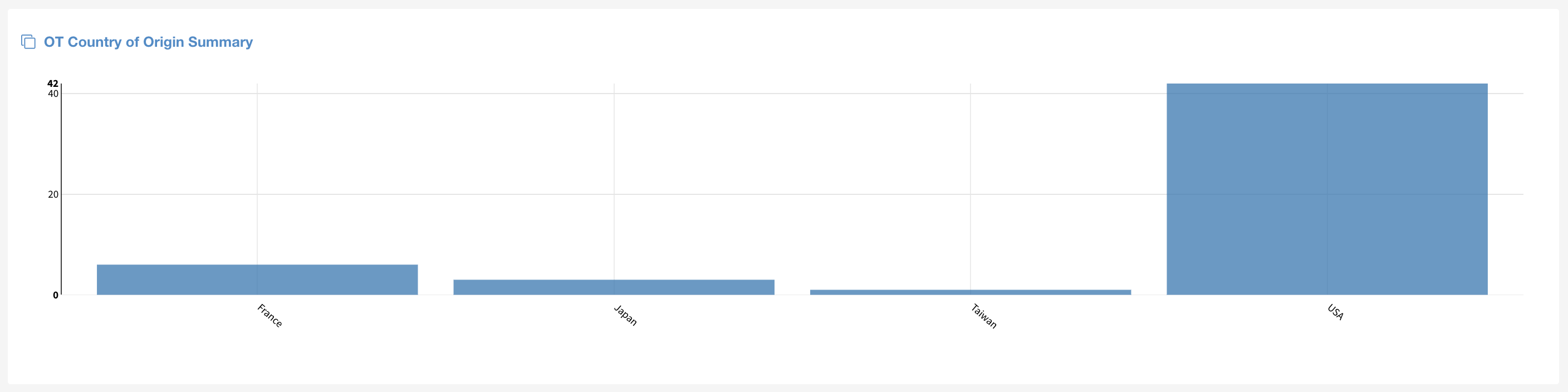
Operational Technology (OT) Dashboard
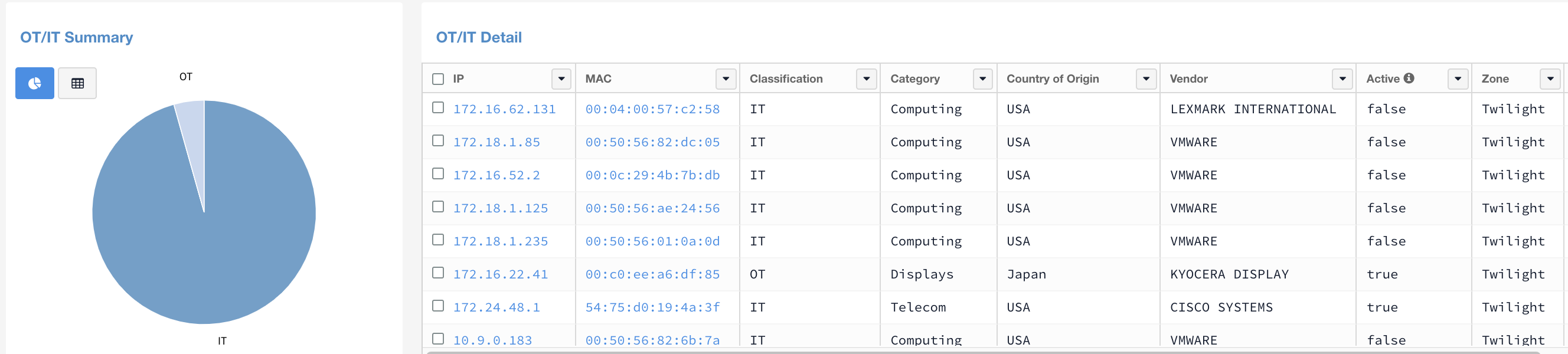
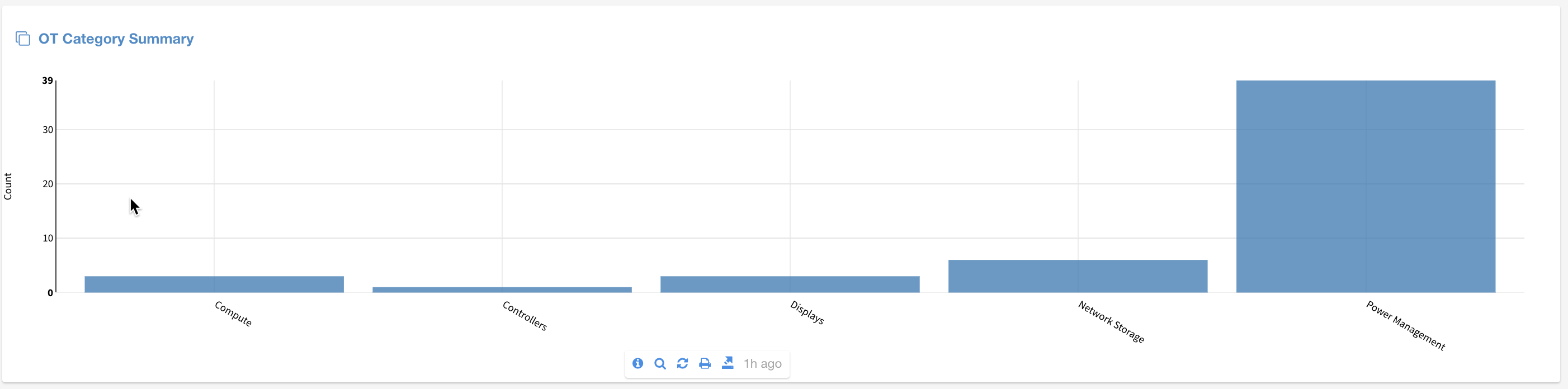
Lumeta introduces the mapping of operational technology vendors to IEEE data. This new capability will give you visibility on the OT devices in your environment.
The out-of-the-box OT dashboard, shown below, will enable you to distinguish between Operational Technology (OT) and Information Technology (IT) while also providing the device details associated with each piece of equipment.
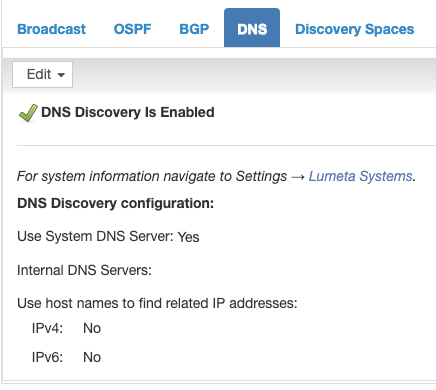
DNS
- Wondering which DNS server is configured on your Command Center?
- Browse to your DNS identifier from Settings > Zones > DNS.
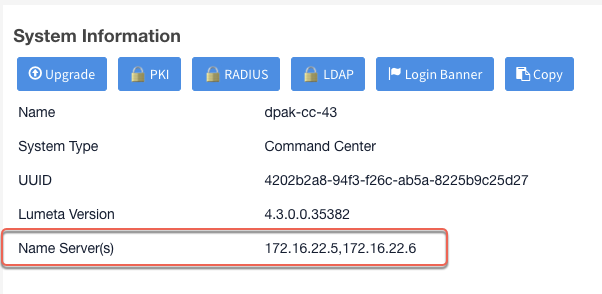
- See the identifier on Settings > Lumeta Systems > System Information
- Browse to your DNS identifier from Settings > Zones > DNS.
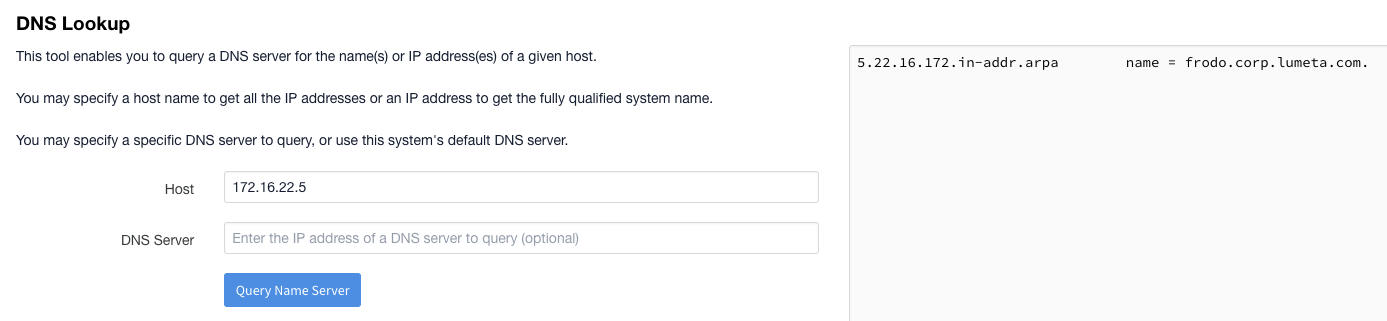
- DNS lookup has been add as a support tool from Settings > Support Tools > DNS Lookup.
DNS configuration commands have been added to the CLI.
Objective Command Check the values via CLI system dns Change the setting manually system dns manual "172.16.22.5,172.16.22.6" Check the current values in the config file cat /etc/resolv.conf Check the help output system dns<tab> system dns manual<?> system dns dhcp<?>
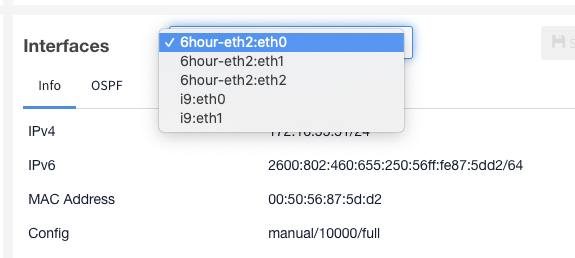
Interfaces
Additional Command Center and Enterprise Scout interfaces may be configured via the CLI or API without having to reinitialize the systems. More granular interface configuration management has been added via CLI submenus. You can see the multiple interfaces on Settings > Lumeta Systems > Interfaces.
CLI
"interface add" and "interface configure
...
API
@POST @Path("/interface/configure")
POST "/api/rest/system/interface/configure?iface=$h{name}"
External Data Connector (EDC)
All External Data Connector (EDC) requests are checked against the Target and Eligible Lists.
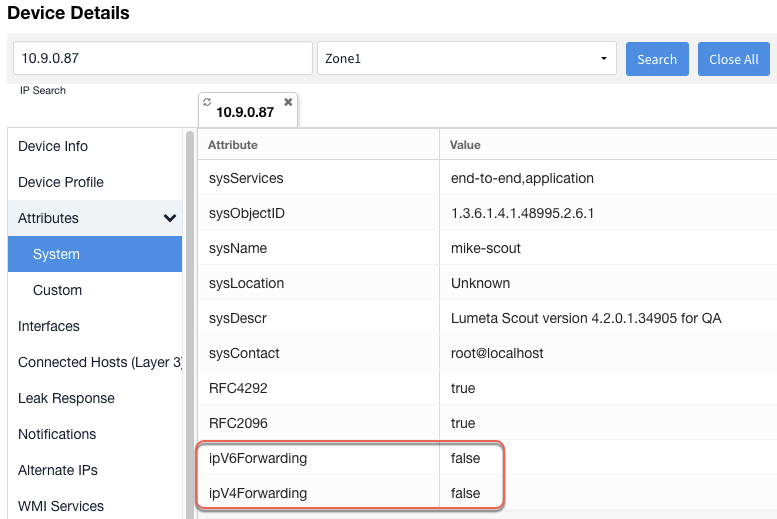
Additional Device Attribute
A "true" or "false" Forwarding attribute displays in the Device Details > Attributes > System column to indicate based on SNMP response whether the device described in that row forwards traffic.
Technical Note
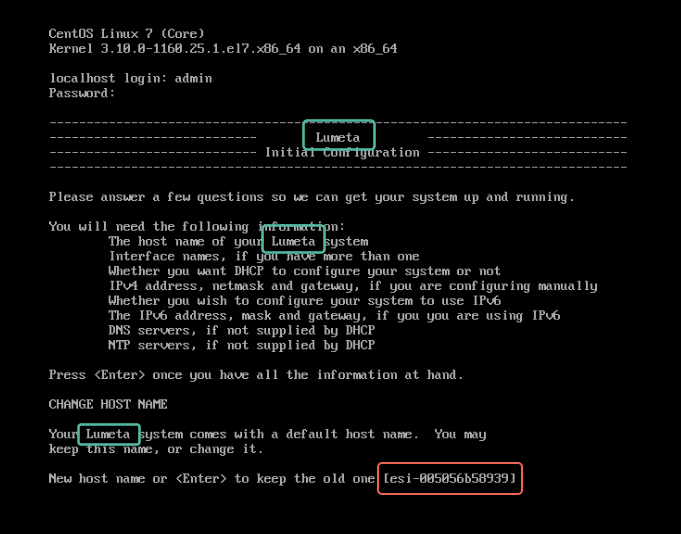
Our product is called "Lumeta" on the GUI, CLI, and API. The legacy names "Spectre" and "ESI" have been removed or replaced. However, the default hostname and root prompt is programmed to be "esi-" followed by the hex encoded IP address. This instance is temporary and will only remain until your system admin changes the host name.
Database Schema
The 4.3 database schema, which shows a visual representation of the Lumeta database, is available here.
...
Lumeta 4.3 resolves Common Vulnerabilities & Exposures (CVEs) and incorporates a variety of security-related (and non-security-related) enhancements. See Security Advisories 4.3 (coming soon) for a list of CVEs resolved in this Lumeta 4.3 release.
| Tip | ||
|---|---|---|
| ||
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228 CVE-2021-44228Apache Log4j2 Remote Code Execution Vulnerability Affecting: Apache Log4j 2.x <= 2.15.0-rc1 The vulnerability is exploited when the Java package 'org.apache.logging.log4j.core.lookup.JndiLookup' or any code that references the JndiLookup Class is leveraged in a very specific way that will cause the software to translate a crafted request into code that can be executed by the server. An example of this behavior
Lumeta’s stand on CVE-2021-44228Lumeta uses version 1.2 of Log4j which is unaffected by CVE-2021-44228 as the JndiLookup Class required for this vulnerability to be exploited was not made available until Log4j version 2.x. (Note: changelog for Apache 2.0-beta9 - https://logging.apache.org/log4j/2.x/changes-report.html#a2.0-beta9"Add JNDILookup plugin. Fixes LOG4J2-313. Thanks to Woonsan Ko." under "Release 2.0-beta9 – 2013-09-14") |
Change Log Updated 9/8/2021
Epic
LUM-2856 - Customer issues targeted in 4.3
LUM-2966 - Updated requirements for the FireMon Integrations
Story
LUM-428 - Make x509 subject and issuer CNs "friendlier"
...
LUM-3026 - Misleading message when doing remote scout upgrade
Bug
LUM-2204 - re-licensing system disables snmpd
...